7 Ways To Secure Your Firm From Business Email Compromise (BEC) Attacks
accounting firm security business email compromise cybersecurity Email Security
Have you ever heard of Business Email Compromise? It’s a scam not unlike phishing.
But while phishing scams can now be easily spotted because of tell-tale red flags in phishing emails, BEC schemes rely on looking like human activity. These schemes typically get control of an email account and then requests for a bank transfer or a similar transaction. They also use wording to make it seem like the request is an ‘Urgent’ one or needs to be completed ‘ASAP.’
BEC schemes resulted in more than $1.7 billion in worldwide losses in 2019, according to the Internet Crime Complaint Center.
As time goes on, hackers come up with more and more elaborate schemes to trick people into giving them sensitive data, and BEC is a classic example of this.
Here are the ways to secure your firm against BEC attacks:
1. Monitor anomalous behaviour.
The increase in remote work means firms are relying on cloud-based services like Microsoft Office, Dropbox, and other document-sharing applications more than ever. Make sure that there are no log-ins at out-of-office hours to these apps.
The Practice Protect portal has a feature that locks out access at your chosen times/days. To learn more about Practice Protect’s Access Management features, visit our page here.
2. Be careful of sudden email account changes.

The migration process when changing a firm’s domain and email platform can leave the mail server open to breaches. If you’ve noticed that an email’s domain has changed, always request verification of an email address if you receive an email from a vendor or even someone from your own firm about a financial matter.
3. Check email addresses for even the slightest discrepancies.

A common trick hackers use is to slightly change email addresses to make them still appear legitimate. The usual culprit is the capital letter “I” being substituted for a lowercase “L”, making them appear similar.
4. Enable MultiFactor Authentication (MFA) for email accounts.

MFA ensures that even if a hacker has access to your email credentials, they would still need access to an authentication app (usually on a mobile device). This adds an extra layer of security. It’s best practice to enable MFA for your firm’s email accounts.
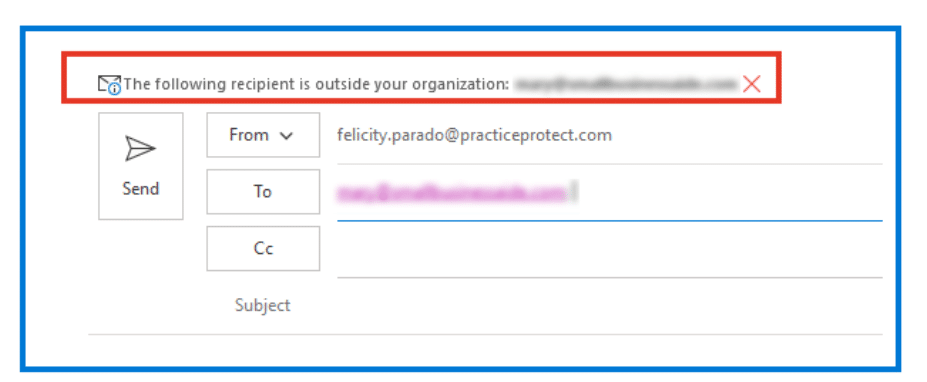
5. Add a banner to messages coming from or sent by team members in your organisation.
Consider enabling this configuration for your email system. The banner should warn users if an email address is coming from someone outside your organisation.
See our example below:
6. Turn on antivirus features that block malicious emails.

Your firm might have antivirus licenses, but are the features that block suspicious emails or phishing emails enabled? Some of us might be guilty of buying an antivirus program but haven’t used it beyond running virus scans.
7. Set up a system within your firm to double-check payment requests.

A good rule of thumb when receiving payment requests or bank transfers is to check with whoever requested it to ensure this is a legitimate request.
Internally, we have a system set up where our Finances team members would always double-check with whoever requested a payment or bank transfer using a chat method. This process ensures that the team member is communicating with whoever requested the transfer using a different channel.

