The Complete Guide to Cybersecurity For Accountants & Bookkeepers [Updated 2023]

Cybersecurity is a word everyone is familiar with these days. The word is synonymous with securing data and devices from malicious actors, but there is a lot more to understand about cybersecurity than just what the word itself means.
In 2023, cybersecurity is one of an accounting or bookkeeping firm’s top priorities. In light of recent major breaches, institutions handling client information are now held liable for any cyber events that could result in data being leaked or taken advantage of.
The first step of being prepared against data breaches is understanding what cyber threats firms are facing. We’ve prepared this guide to be the one-stop accounting and bookkeeping firms can refer to when trying to understand cybersecurity and why it matters.
Understanding the Risks: Types of Threats to Firms
Phishing
One of the most common types of cybercrime is phishing. Phishing emails aim to trick users into sharing sensitive information or taking actions that could put a network’s security at risk. The objective of these attacks is to gain access to accounts, breach a network, or deploy malware. In some cases, convincing phishing emails can even lead to the transfer of funds into an attacker’s account.
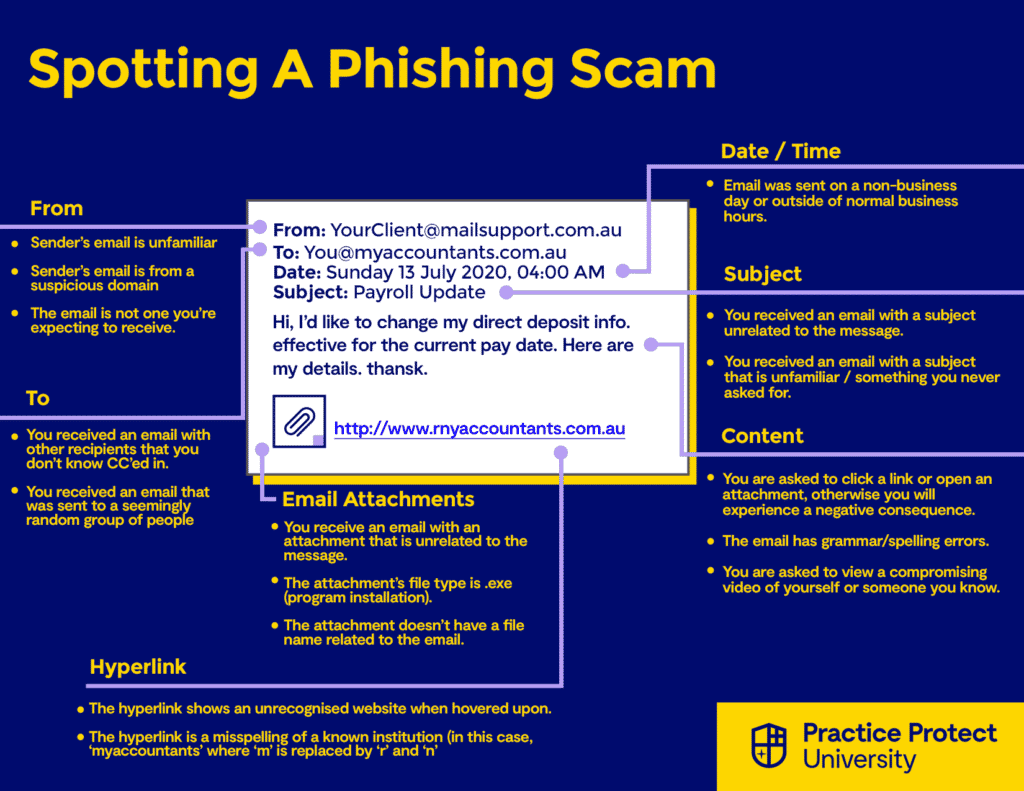
3 main goals of a phishing scam:
- Get a target to click a link
- Get a target to download an attachment
- Get a target to give up their credentials
Malware
Short for ‘malicious software,’ as the name suggestions, malware is any software that intends to cause harm to a device or network. Malware can usually be found in email attachments, fraudulent links, ads, or on harmful websites.
Common types of malware:
- Virus: This type of malware, like the name suggests, infects programs. It spreads once an infected file is launched or opened, corrupting, deleting, or moving files.
- Worm: A type of malware that attacks a device’s hard drive or memory. They usually come from links or email attachments.
- Trojan: Like the Trojan horse of Greek mythology, the Trojan malware pretends to be a legitimate program that users can install. Upon installment, the program will then wreak havoc on the device it was installed on.
- Ransomware: One of the most popular malware types, ransomware attacks encrypt a target’s data and holds it for ransom.
- Spyware: This type of malware, like its name suggests, spies on or monitors the activities of a user. A common kind of spyware is a keylogger, a malicious program that records keystrokes on a keyboard, and is typically used to harvest credentials or passwords.
- Spam/Adware: These are the unwanted ads that pop up on websites. While harmless if not interacted with, they can still slow down a device’s performance. However, once clicked on, adware can lead to more harmful malware being downloaded onto a device.
- Rootkits: A rootkit is a program that provides administrative access to a device, while remaining undetected. It can impact a device’s performance, as well as put the data stored in the device at risk.
Ransomware
Ransomware is a type of malicious software (malware) that is popular among cyber criminals, and is expected to be even more popular in 2023. Ransomware attacks featured heavily in 2022’s headlines because of attacks on big corporations.
However, underneath these high-profile attacks, small and medium businesses are also being hit by ransomware attacks. 37% of companies hit by ransomware had fewer than 100 employees, which is proof that this type of threat is one that accounting firms should be aware of.
Social Engineering
Social engineering is the umbrella term for malicious activities that leverage psychological manipulation to deceive people into making security errors or divulging sensitive information.
Social engineering is also called “human hacking” as it doesn’t exploit technical errors but rather targets the biggest security risk, humans. Social engineering is all about tricking people into giving access or credentials that cybercriminals then exploit.
Types of common social engineering scams:
- Impersonation: Attackers may pretend to be a client or colleague via digital communication in order to gain access to sensitive financial information or to steal money from clients. Impersonation is a key aspect of many types of social engineering scams.
- Business Email Compromise (BEC): Similar to the above, an attacker will impersonate a senior executive or a vendor to request for wire transfer or sensitive information. This particular scam focuses on email as the method to exploit accountants and bookkeeper through email.
- Pretexting: This social engineering attack involves someone misusing their role to gain access to sensitive data. The malicious actor uses their role or title within the organization to gain trust and acquire credentials, client data, or other sensitive information that they otherwise would not have access to. This attack most often happens with insider threats (someone from within the organization attempting to steal or compromise data).
- Smishing and Vishing: This attack uses SMS text messages or phone calls to impersonate a bank or government official in order to trick accountants or bookkeepers into providing sensitive information.
- Baiting: This social engineering scam is one you might have encountered. Baiting involves scammers luring targets into providing sensitive information in exchange for something valuable. Pop-up ads that promise free games, music, software, or video downloads if they’re clicked is a form of baiting.
- IT/Tech support scams: This scam involves hackers pretending to be someone from tech support or your IT provider. The hacker would then request that the target allow them access to their computer, or to download software containing malicious code.
- Scareware/Fraudware/Deception Software: A form of social engineering that uses the element of fear to get a target to deploy malicious software in their device.
- Tailgating: Attackers may use physical means to gain access to a building or restricted area by following an authorized person.
Being aware of these scams is the best form of defence, so that you or your team are able to identity them when they occur and not fall victim.
A popular security methodology called Zero Trust is gaining traction as it helps defend against hacks exploiting human error. A Zero Trust architecture assumes that all users, devices, and applications are untrustworthy and can be compromised. Therefore only users that have been authenticated using multi-factor methods can get access to data, and only to the data they need.
Insider Threats
As the name indicates, this type of threat is a security risk that comes from within the firm itself. Any current or former staff member who has access to sensitive information and then misuses this access is classified as an insider threat.
Insider threats are classified into the following:
- Unintentional threats: As the name suggests, this involves employees who expose an organization to a cyber threat due to negligence/carelessness or an accident.
- Intentional threats: This insider threat results from the actions of an individual who deliberately sets out to misuse data they have access to.
- Third-party threats: These are typically vendors or contractors who are not employees, but have some level of access within the firm.
Denial of Service (DoS) Attacks
A Denial of Service (DoS) attack is an attempt to shut down a device or network and render it unavailable to users. This attack is accomplished by overloading the targeted device or network with traffic until the target cannot respond or crashes.
Affected services may include email, websites, online accounts, or other services that rely on the affected computer or network.

Implementing Technical Security Measures
Now that we’ve outlined the most common cyber threats accounting and bookkeeping firms face, it’s time to discuss how firms can safeguard against these threats.
Identity & Access Management (IAM)
Identity and access management is an umbrella term for software used to manage user access in a firm or organization.
Accountants and bookkeepers can leverage identity and access management solutions to authenticate, authorize, and audit access to applications and systems. These solutions, which are often part of an identity and access management suite, can help safeguard security and reduce risk by controlling access to on-premises and cloud-based applications and services. Additionally, they can ensure the right users have the right resources at the right times and for the right reasons.
Identity and access management solutions can include tools for granting access privileges and tracking login attempts and access activity.
Benefits of Identity & Access Management for accounting and bookkeeping firms
IAM software can be used to record and manage user identities, and then granting access based on those identities. IAM goes beyond simple password management software, and firms who use an IAM solution gets the following benefits:
- Access privileges are determined according to policies assigned to users, and all users and services are then properly authenticated, authorised, and audited within the IAM system.
- Properly managed identities means that firms have greater control over user access
- IAM makes it easier for a firm to monitor policies for user authentication and privileges
Email Systems
Email is the one of the applications that an accounting or bookkeeping firm uses the most. It’s a primary communication channel—whether communicating with colleagues or with clients, email is used by the CEO, practice manager, and staff.
An accounting or bookkeeping firm’s email system contains a treasure trove of client data, and this is exactly why cyber criminals target email. This, coupled with the fact that email providers have to balance login convenience with security (like Multi-Factor Authentication or geo-fencing), makes email systems very attractive to malicious actors.
Email security breaches continue to pose a major risk to businesses. These malicious acts may include phishing, malware and spam assaults, ransomware break-ins, and Business Email Compromise. 2023 is the year that SMBs are reminded to secure their email systems against cyber criminals attempting to exploit the data in email systems.
Best practices for securing email systems:
- Set up Single Sign-On (SSO) authentication for emails at your firm
- Disable legacy mailbox protocols like SMTP, POP, and IMAP
- Mandate that staff have strong passwords for their email
- Limit administrator privileges only to necessary users
Devices
Accountants and bookkeepers understand the importance of keeping client data protected. Cyber security is a critical concern for any accounting firm, and a significant portion of that concern sits with the tool employees use to complete all their work, the desktop or laptop.
As every device connects into a larger digital network within the firm, it only takes one device being compromised to potentially infect the entire network. Therefore device security becomes an important layer of defense is safeguarding devices against threats like malware, ransomware and viruses that look to access and compromise valuable data.
There are reactive and proactive technologies to deal with these threats. The Practice Protect Device Hub provides uses the latest technologies including a virtual firewall and AI-powered threat detection to prevent threats including malicious code that hasn’t been detected before worldwide, called a day-zero threat. Learn more.
Creating Strong Cybersecurity Practices
[US] IRS 4557 Data Security Plan
The IRS, in conjunction with state tax agencies and the accounting industry, has developed Publication 4557 to provide legal requirements for data security and protection to help combat cyber criminal activity. Tax accountants must keep up with these guidelines, as they are continually evolving to meet the changing needs of cybersecurity. Not doing so can leave accountants in a vulnerable position, facing potential data breaches and IRS penalties.
Professional accountants should be aware of the risks associated with their data, and ensure they are compliant with the guidelines outlined in Publication 4557.
Learn more about IRS 4557 and a compliant Data Security Plan here.
Data & Internet Usage Policy
As accountants, it is essential to have a Data & Internet Usage Policy that sets expectations for employees when it comes to accessing client data and the internet.
This policy should outline:
- The expected use of passwords and logins
- Permitted access of any applications or networks that your firm uses
- Proper email use and access
- How work-issued equipment is used and stored
Training Employees
According to Verizon’s 2022 Data Breaches Investigation Report, 82% of data breaches involve a human element. Human error, such as not recognizing a phishing email, can be just as dangerous as any other security threat.
Training employees and making sure they are aware of basic cybersecurity practices goes a long way towards securing your firm.
To ensure your team is equipped to handle these risks, it is important to invest in proper training. Here are some steps you can take to start your training program:
- Establish best practices for cybersecurity. Provide your team with documents that outline the do’s and do not’s of cybersecurity. The Practice Protect University offers useful resources such as the Employee Cyber Safe Guidelines Pack and best practice checklists.
- Remind staff to create strong passwords. Stress the importance of creating complex passwords for work-related emails and applications.
- Educate employees on potential cyber threats. Equip employees with the knowledge to identify and address common cyber threats, such as phishing emails. We recommend that you subscribe to websites that provide updates to scams like Scamwatch (the Australian government’s website for scam awareness) or the FTC’s Consumer Alerts service.

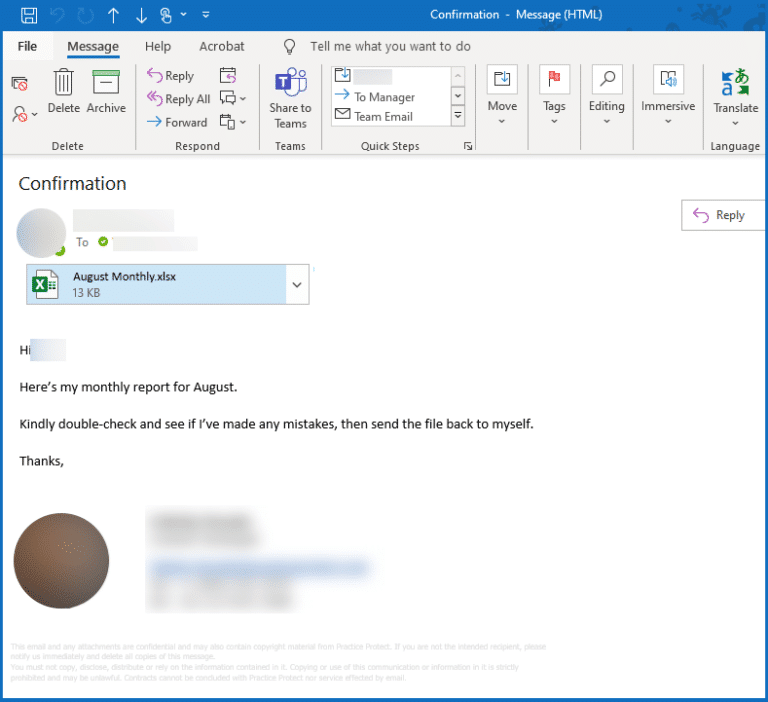
Responding to a Data Breach
A cybersecurity incident is an unwelcome or unforeseen event, or a sequence of such occurrences, that could potentially disrupt business activities. A data breach is a type of cybersecurity incident where Personally Identifying Information (PII) is accessed or leaked by a malicious actor.
Nobody wants to think about a cybersecurity incident like a data breach happening at their firm. However, it’s best to be prepared with a plan on how to respond to such an incident if it does occur. The worst-case scenario isn’t that your firm suffers a data breach, but that your firm has no plan of action if a data breach does occur.
Personally Identifying Information (PII) includes:
- Tax File Numbers / Tax Identification information numbers
- Social Security Numbers
- Credit card information
- Payroll Information
- Medical Information
- Other personal information (dates of birth, addresses, phone numbers)
Identifying a Data Breach
Identifying when a firm has suffered a data breach is crucial in the subsequent response. The longer a breach goes undetected, the more damage it can do to a business.
Warning signs that may indicate that a data breach has occurred within your business should not be ignored. Professional investigation should be conducted if any of the following red flags are present:
- Alerts from antivirus software or malware protection software that they have been disabled
- Frequent application or system crashes
- Unusual user activity (user logging in at non-business hours or from unusual locations)
- Unexpected password changes or user account lockouts
- Unexpected pop-ups appearing while browsing
- A message from a cyber criminal demanding payment in exchange for data decryption (ransomware)
Assessing a Data Breach
Once the data breach has been identified, the next step is to evaluate the incident. This includes identifying the sensitivity of the PII compromised, how much PII was compromised and how many clients were affected, and how likely it is that the compromised PII can cause harm.
The response to the breach will depend on the findings of this assessment stage, and will dictate whether a firm has to bring in cybersecurity experts or consultants to aid in the response and remediation.
Developing A Response Plan
A data breach response plan is essential for all firms, regardless of the size of the firm or the industry. Having a data breach response plan in place enables them to react quickly to a breach, thus reducing its potential impact on affected individuals, associated costs and reputational damage.
The data breach response plan provides a framework for the roles and responsibilities involved in managing a data breach. To ensure that all staff are aware of the plan, it should be easily accessible and be able to be accessed on short notice.
What the data breach response plan should cover:
- An explanation of what constitutes a data breach
- A strategy for how to contain, assess, and manage data breaches
- The roles staff will take in the case of a suspected data breach
- Documentation for data breach incidents
- A review of how the data breach occurred and how to prevent it from happening again
Conclusion & Resources
In 2023, cybersecurity will be even more vital to the success of businesses, as well as individuals. Companies that don’t prioritise cybersecurity will leave themselves vulnerable to data breaches and malicious attacks.
For accounting and bookkeeping businesses who deal with client data on a daily basis, the need for cybersecurity is essential. Without a cybersecurity solution in place, companies are at risk of data theft and unauthorised access to their systems. This could lead to significant financial losses, reputational damage, and even regulatory fines.
We have also put together a list of resources you can use for further research or education for your staff:
Data Breach Responses
- Federal Trade Commission – Data Breach Response: A Guide For Business
- Australian Government OAIC – Data breach preparation and response
Email Security
- 7 Email Security Best Practices For Accounting & Bookkeeping Firms
- 7 Ways To Secure Your Firm From Business Email Compromise (BEC) Attacks
- Email Security For Accountants: How to secure your most vulnerable application
Want to see how Practice Protect can help your firm put these security measures in place? Book an obligation-free call with our team today.

